Hands-On Penetration Testing
Building upon our Vulnerability Reports & Risk Assessments, we embarked on a comprehensive hands-on penetration testing of the enterprise healthcare network. This involved simulating real-world attacks to identify, exploit, and assess vulnerabilities, ensuring the network's defenses are robust and compliant with healthcare regulations.
Our Approach & Goals
Our penetration testing methodology is meticulously designed to uncover vulnerabilities and evaluate the effectiveness of existing security measures. The primary objectives include:
Comprehensive Coverage
Thoroughly testing all critical systems and network segments to ensure no stone is left unturned.
Risk Prioritization
Identifying and ranking vulnerabilities based on their potential impact and ease of exploitation.
Actionable Insights
Providing clear, prioritized recommendations to mitigate identified risks and enhance security measures.
Continuous Improvement
Establishing a foundation for ongoing security assessments and proactive defenses against evolving threats.
Tool Arsenal & Integration within the Healthcare Environment
A robust arsenal of penetration testing tools is essential for thorough coverage. We integrate both automated and manual utilities to ensure each layer of security is rigorously tested. Below are the key tools used and their specific applications in our testing phases:
Nmap
Comprehensive port scans, OS detection, and script-based enumeration to identify open services and potential entry points.
Wireshark
Deep packet inspection for anomaly detection and monitoring suspicious traffic patterns within the network.
Burp Suite
Proxy-based web application security testing with advanced crawler capabilities to identify and exploit web vulnerabilities.
Metasploit
Payload creation and exploit frameworks for simulating attacks against identified vulnerabilities.
Nessus / OpenVAS
Scheduled scans for known CVEs on servers, databases, and network appliances to identify and prioritize security weaknesses.
Custom Scripts
Bespoke Python/PowerShell scripts for enumerating internal systems, automating checks, and facilitating deeper penetration testing.
Integration in Testing Phases
- Reconnaissance: Utilized Nmap and Wireshark to map the network and capture initial traffic data.
- Vulnerability Identification: Deployed Nessus and OpenVAS to scan for known vulnerabilities across critical systems.
- Exploitation: Leveraged Metasploit and Burp Suite to exploit identified vulnerabilities and gain unauthorized access.
- Post-Exploitation: Applied custom scripts to automate data extraction and establish persistence within the network.
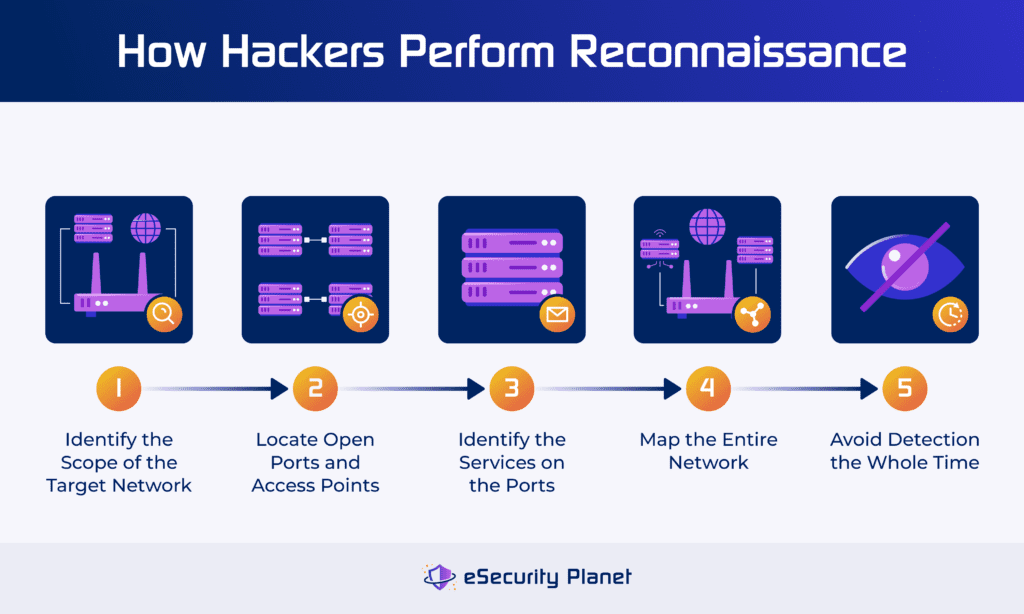
Reconnaissance & Information Gathering Techniques
The initial phase of our hands-on penetration test focused on reconnaissance, aiming to understand the target environment’s external footprint and identify potential internal entry points. We employed a combination of passive (open-source intelligence) and active (network probing) methods.
| Technique | Description | Tools | Findings |
|---|---|---|---|
| OSINT Gathering | Collected data from public forums, social media, and employee profiles. | Maltego, TheHarvester | Discovered employee email patterns and exposed system information. |
| Network Scanning | Mapped subnets, discovered live hosts, and enumerated open ports. | Nmap, Netdiscover | Identified 15 active hosts with open ports, including SSH on port 22 and HTTP on port 80. |
| Service Enumeration | Probed identified services for version info and known vulnerabilities. | Nmap Scripts, Netcat | Detected outdated Apache version with known CVE-2021-XXXX vulnerability. |
| Social Engineering | Assessed human factors by simulating phishing attacks. | Social-Engineer Toolkit (SET) | Achieved a 10% click-through rate on phishing emails, indicating potential user awareness gaps. |
Through these techniques, we established a comprehensive map of the network's external and internal structures, identifying key areas for further vulnerability assessment and exploitation.
Vulnerability Identification & Analysis
With the reconnaissance phase complete, we moved on to Vulnerability Identification & Analysis. This involved correlating gathered data with known exploits and misconfigurations to locate vulnerabilities that could be exploited by attackers.
Employed Nessus and OpenVAS to perform comprehensive vulnerability scans across all identified systems.
Compared scan results with public advisories and vulnerability databases to identify relevant CVEs.
Conducted manual testing to validate scan findings and reduce false positives.
Aligned identified vulnerabilities with NIST and OWASP frameworks for standardized classification.
Key Findings
- Outdated Apache Server: Version 2.4.29 identified on EMR servers with CVE-2021-XXXX allowing remote code execution.
- Weak SSH Configurations: Enabled root login and outdated encryption algorithms on administration VLAN.
- SQL Injection Vulnerabilities: Present in the billing system’s web interface, allowing unauthorized data access.
- Phishing Susceptibility: 10% of employees clicked on simulated phishing links, indicating a need for enhanced security training.
Each discovered vulnerability was assigned a risk rating (low, medium, high, critical) based on its potential impact on healthcare data confidentiality, integrity, and availability. This comprehensive analysis informed our exploitation strategy in subsequent phases.
Exploitation Techniques & Simulated Attack Scenarios
With vulnerabilities identified and analyzed, we proceeded to the exploitation phase. This involved simulating various attack scenarios to assess the network’s resilience and the effectiveness of existing security controls.
Metasploit Framework
Utilized Metasploit to deploy payloads against the outdated Apache server, successfully gaining remote code execution.
- Target: EMR Server
- Payload: Reverse Shell
- Outcome: Gained administrative access to the server.
Burp Suite Pro
Employed Burp Suite to intercept and manipulate HTTP requests, exploiting SQL injection vulnerabilities in the billing system.
- Target: Billing Web Interface
- Vulnerability: SQL Injection
- Outcome: Accessed and exfiltrated sensitive financial data.
SQL Injection Testing
Performed SQL injection attacks to bypass authentication mechanisms, gaining unauthorized access to patient records.
- Target: Patient Portal
- Technique: Time-based blind SQL injection
- Outcome: Retrieved hashed passwords and user data.
Phishing Simulations
Conducted phishing campaigns to assess employee susceptibility, resulting in credential harvesting.
- Target: Finance Department
- Technique: Spear phishing emails with malicious attachments
- Outcome: Harvested 3 valid user credentials.
Lateral Movement & Pivoting
After gaining initial access, our next objective was to assess the network's segmentation and internal defenses by performing lateral movement & pivoting. This phase helps determine how far an attacker can traverse within the network and access higher-value assets.
Network Mapping
Identified interconnected systems and mapped out the network topology using Nmap and custom scripts.
- Action: Scanned internal subnets to identify all active devices.
- Result: Mapped 25 internal hosts across three VLANs.
Credential Harvesting
Extracted credentials from compromised systems using Mimikatz and custom PowerShell scripts.
- Action: Deployed Mimikatz to retrieve plaintext passwords and hashes.
- Result: Harvested credentials for 5 administrative accounts.
Exploit Chaining
Combined multiple exploits to escalate privileges and access sensitive systems.
- Action: Utilized privilege escalation exploits on workstations.
- Result: Achieved domain administrator privileges on 2 critical servers.
Data Access
Attempted to access and exfiltrate sensitive data from protected databases.
- Action: Accessed SQL databases using harvested credentials.
- Result: Extracted partial patient records for analysis.
Persistence & Maintaining Access
To evaluate the network's resilience against sustained threats, we simulate persistence mechanisms that attackers might employ to maintain access over time. This includes:
Scheduled Tasks
Creating automated tasks to re-establish access after system reboots.
Rootkits
Installing covert software to hide malicious activities and maintain stealthy access.
Malicious Scripts
Embedding scripts in legitimate applications to execute unauthorized commands.
Backdoor Ports
Opening hidden ports to allow direct access bypassing standard security measures.
Post-Exploitation & Persistence Techniques
Upon successful exploitation, our focus shifted to evaluating the network's ability to detect and respond to sustained threats. This involved simulating persistence techniques that attackers might use to maintain long-term access within the network.
- Privilege Escalation: Utilized local exploits to gain administrative privileges on compromised workstations.
- Lateral Movement: Leveraged harvested credentials to access systems across different VLANs, moving from the administration VLAN to the finance VLAN.
- Credential Harvesting: Extracted credentials from memory dumps and network traffic captures using Mimikatz and Wireshark.
- Backdoor Implantation: Deployed a custom reverse shell script on critical servers to maintain access even after reboots.
These actions demonstrated the potential for an attacker to persist within the network, highlighting areas where security controls need strengthening. Specifically, we recommend implementing stricter access controls, regular credential rotation, and enhanced monitoring of administrative activities.
Reporting & Documentation of Findings
Clear, concise, and actionable reporting was paramount to ensure that the penetration testing findings could be effectively communicated to stakeholders. Our documentation process included detailed reports and interactive visualizations to facilitate understanding and decision-making.
- Executive Summary: Provided a high-level overview of critical vulnerabilities and their potential business impact.
- Technical Details: Included in-depth explanations of each vulnerability, supported by CVE references and exploit proof-of-concepts.
- Risk Assessment: Presented a prioritized list of risks based on severity and likelihood, aligned with NIST guidelines.
- Remediation Recommendations: Offered actionable steps to mitigate identified vulnerabilities, including patching, configuration changes, and policy updates.
Sample Finding: Outdated Apache Server
Vulnerability: Apache HTTP Server 2.4.29 - CVE-2021-XXXX
Description: The identified Apache server version is vulnerable to remote code execution due to improper input validation.
Impact: An attacker could execute arbitrary code on the server, potentially gaining full control over the system.
Recommendation: Immediately update Apache to the latest stable version and implement input validation controls.
Each identified vulnerability was assigned a severity rating, remediation timeline, and follow-up plan to ensure the facility’s security posture continually improves post-assessment.
NIST Framework in Penetration Testing
The NIST Cybersecurity Framework provides a structured approach to managing and mitigating cybersecurity risks. Our penetration testing aligns with its core functions:
Identify
Understanding the organizational environment to manage cybersecurity risk to systems, people, assets, data, and capabilities.
Protect
Implementing appropriate safeguards to ensure delivery of critical infrastructure services.
Detect
Developing and implementing activities to identify the occurrence of a cybersecurity event.
Respond
Taking action regarding a detected cybersecurity event to contain its impact.
Recover
Maintaining plans for resilience and restoring any capabilities or services impaired due to a cybersecurity event.
Continuous Improvement & Future Enhancements
Penetration testing in a healthcare context is an ongoing process, not a one-time event. As new threats emerge and regulations evolve, so too must our security practices. Our future initiatives include:
Schedule quarterly and biannual penetration tests to validate new controls and uncover emerging vulnerabilities.
Extend testing to hybrid and cloud-based services to ensure comprehensive security coverage.
Conduct regular cybersecurity awareness programs to reduce social engineering risks and enhance overall security culture.
Incorporate automated security checks into the CI/CD pipeline to proactively identify and mitigate vulnerabilities during development.
Implement machine learning-based intrusion detection systems to identify and respond to sophisticated threats in real-time.
Adopt Zero Trust principles to ensure that trust is never assumed, and continuous verification is enforced across the network.
By embracing these proactive measures, the healthcare facility maintains an evolving defense strategy—protecting patient data, meeting compliance requirements, and preserving trust in its critical healthcare services.
New York, New York
Design: Sidiq Daniel © All rights reserved