Vulnerability Reports & Risk Assesments
Categorizing critical systems, assessing vulnerabilities, and identifying risks to prepare for effective penetration testing.

Overview
In this section, I provide an overview of the vulnerability reports and risk assessments conducted on the enterprise healthcare network. This groundwork is essential for understanding the critical areas that require attention before initiating penetration testing.
Critical Systems Categorization
Categorizing systems based on their criticality and sensitivity helps in prioritizing security measures. Below is a categorization of systems holding PHI, company data, and other sensitive information.
| System | Category | Data Type | Importance |
|---|---|---|---|
| EMR Servers | Clinical | PHI | High |
| Billing Systems | Operational | Financial Data | Medium |
| Admin Workstations | Administrative | Confidential | High |
Vulnerability Assessment Overview
The vulnerability assessment identifies potential weaknesses within the network infrastructure. This assessment leverages various tools to scan and detect vulnerabilities across all categorized systems.
Risk Identification and Analysis
Identifying and analyzing risks associated with each vulnerability is crucial for effective mitigation. This section outlines the methodologies used for risk assessment.
Severity Matrix and Heatmaps
The severity matrix and heatmaps provide a visual representation of vulnerabilities based on their impact and likelihood, aiding in prioritizing remediation efforts.
Asset Inventory and Classification
Maintaining an accurate asset inventory is essential for effective vulnerability management. This inventory classifies assets based on their criticality and sensitivity.
| Asset | Type | Classification | Owner |
|---|---|---|---|
| EMR Server | Server | PHI | IT Department |
| Billing Workstation | Workstation | Financial | Finance Department |
Vulnerability Distribution
Understanding the distribution of vulnerabilities across different systems helps in identifying patterns and areas requiring immediate attention.
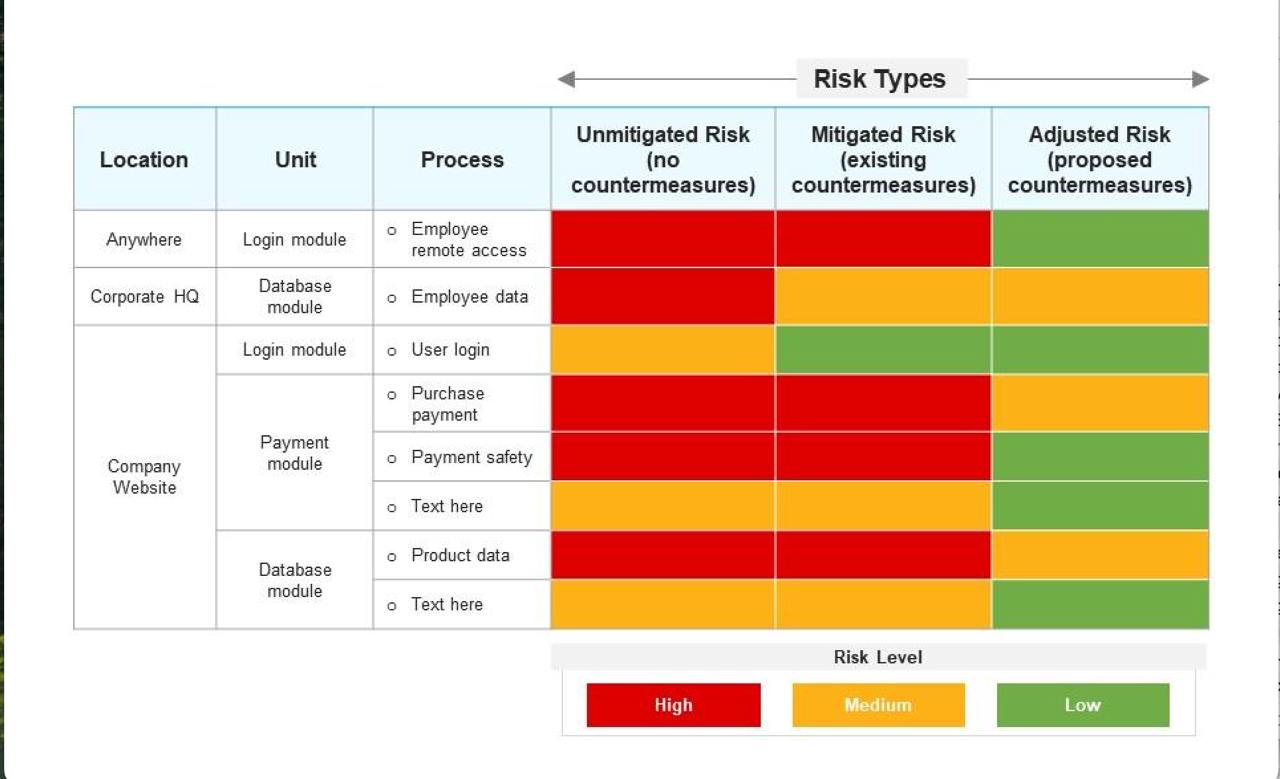
Risk Prioritization
Prioritizing risks ensures that the most critical vulnerabilities are addressed first, optimizing resource allocation and enhancing security posture.
| Vulnerability | Impact | Likelihood | Risk Score | Priority |
|---|---|---|---|---|
| Unpatched EMR Server | High | High | 9 | Critical |
| Weak Admin Passwords | Medium | High | 7 | High |
Visualization of Potential Threats
Visual representations of potential threats help in comprehending the attack vectors and their possible impacts on the network infrastructure.
Summary & Next Steps
This comprehensive vulnerability report and risk assessment provide a clear roadmap for addressing the identified weaknesses within the enterprise healthcare network. By categorizing critical systems, assessing vulnerabilities, and prioritizing risks, we are well-prepared to undertake effective penetration testing.
Moving forward, the next phase involves executing penetration tests on the prioritized vulnerabilities to validate their exploitability and impact. The findings from these tests will further inform our mitigation strategies and enhance the overall security posture of the network.
New York, New York
Design: Sidiq Daniel © All rights reserved