Network Infrastructure Design & Framework
Explore an enterprise-grade Network Infrastructure Design & Framework tailored for secure, scalable, and HIPAA-compliant healthcare operations

Introduction
In this section, I highlight the enterprise-grade network infrastructure I designed for the healthcare facility. The primary aim is to ensure secure, scalable, and HIPAA-compliant operations that protect patient data while maintaining critical services.
Building upon my previous project (upgrading from a SOHO environment), I’ve refined the architecture with robust segmentation, redundancy, and integrated security measures informed by NIST guidelines.
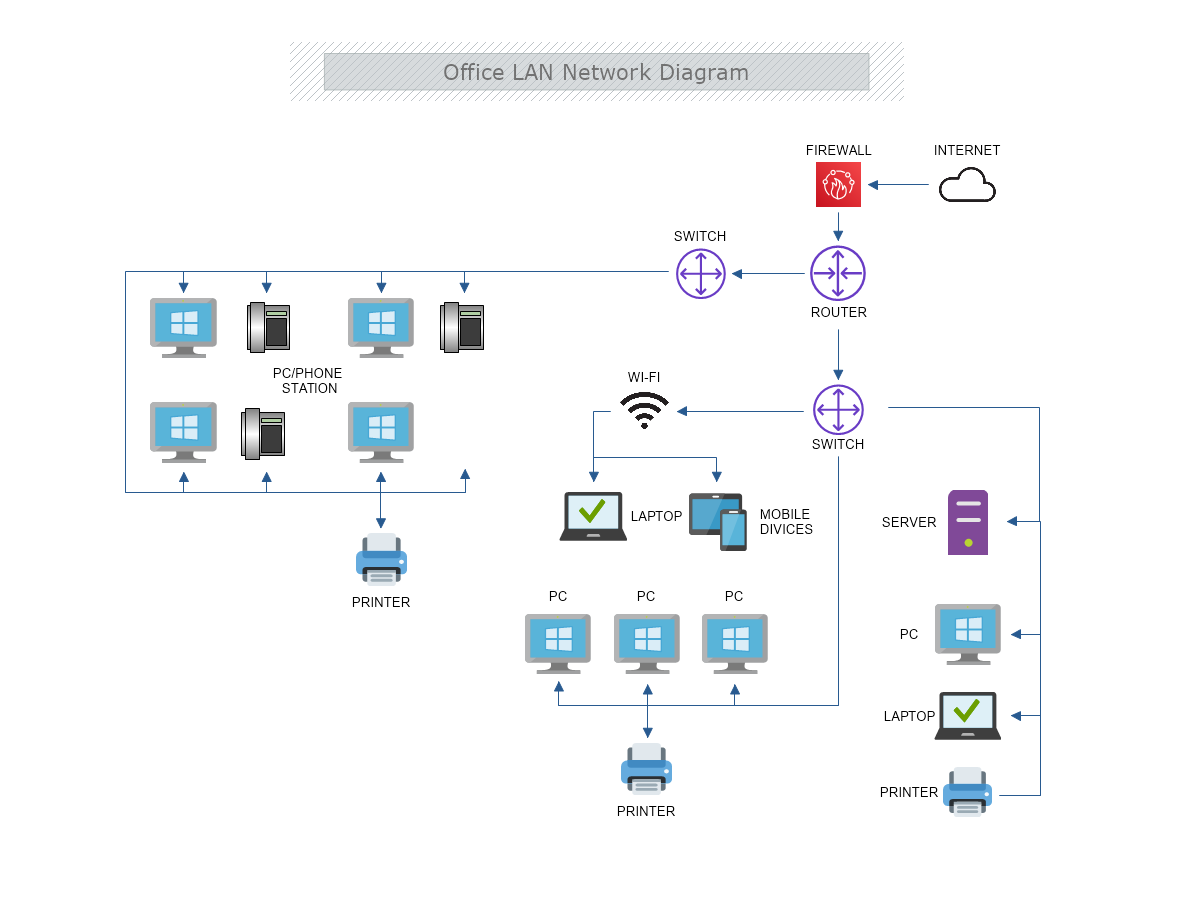
Current Infrastructure Overview
The facility's network is divided into multiple VLANs to separate internal services, administrative functions, and patient data from less critical segments. A dedicated DMZ hosts external-facing services (e.g., patient portal), while core switches and firewalls enforce access control. Key devices include:
- Core Switches for intra-VLAN routing
- Next-Gen Firewall for threat inspection
- WLAN Controllers for secure wireless access
- Proxy Servers for outbound traffic filtering
Device & Segment Inventory
Below is a condensed inventory of critical segments, associated devices, and primary security configurations:
| Segment | Devices | Security Configurations |
|---|---|---|
| VLAN 10 (Admin) | Admin Workstations, Domain Controller | Strict ACLs, RBAC, MFA for admin accounts |
| VLAN 20 (Clinical) | EMR Servers, Medical Devices | Encrypted traffic (TLS), Endpoint hardening |
| DMZ | Web Server, Patient Portal | Reverse proxy, WAF rules, separate firewall zone |
| VLAN 30 (Guest Wi-Fi) | Guest Access Points | Isolated SSIDs, Captive portal, Rate limiting |
Security Mechanisms in Place
Firewall & IDS/IPS
Inspects inbound/outbound traffic for malicious signatures, blocks known attack vectors, and quarantines suspicious hosts.
Role-Based Access Control
Ensures only authorized personnel can access critical segments (PHI, medical device VLAN) based on roles & responsibilities.
Strong Authentication
MFA and password complexity policies reduce the risk of unauthorized logins, especially for administrative accounts.
Pros & Cons of the Current Architecture
Pros
- Network segmentation reduces lateral movement
- Dedicated DMZ for external services lowers internal exposure
- Adoption of NIST & HIPAA guidance ensures compliance
Cons
- Complex VLAN & firewall rules can be challenging to manage
- Legacy devices still lacking modern security features
- Some staff & IoT endpoints not fully integrated into RBAC
Potential Entry Points & Lateral Movement
Understanding how an attacker might infiltrate the network is crucial for effective defense. From phishing emails leading to compromised workstations to exposed services in the DMZ, I’ve identified these likely entry avenues:
- Unpatched systems on the Admin VLAN
- Phishing attempts targeting clinical staff
- Weak Wi-Fi encryption on guest networks
- Improperly secured remote access or VPN endpoints
Once inside, attackers could pivot laterally to other VLANs if ACLs or segmentation rules are insufficient.
Data Classification & Asset Mapping
To protect vital information, I identified and categorized key assets according to criticality and sensitivity. For instance:
NIST & HIPAA Framework Integration
Throughout the network design process, I followed NIST CSF and HIPAA Security Rule guidelines. Key implementations include:
- Identify: Asset inventory, classification of PHI
- Protect: Network segmentation, RBAC, encryption in transit
- Detect: Intrusion detection systems, log monitoring
- Respond: Incident response plan for rapid breach containment
- Recover: Disaster recovery testing, system backup strategies
This ensures every layer of the infrastructure meets or exceeds industry standards for handling protected health information.
Visualizing the Network
Below is a simplified diagram demonstrating VLAN segmentation, firewall placements, and core routing. Use the carousel to explore various angles of the topology.
Next Steps & Navigation
This Network Infrastructure Design & Implementation sets the foundation for secure healthcare operations. Having established a segmented environment with robust security controls, I will next evaluate the system for vulnerabilities and potential risks.
In the upcoming Vulnerability Reports & Risk Assessments page, I’ll detail discovered weaknesses, rank them by severity, and propose strategic remediation plans.