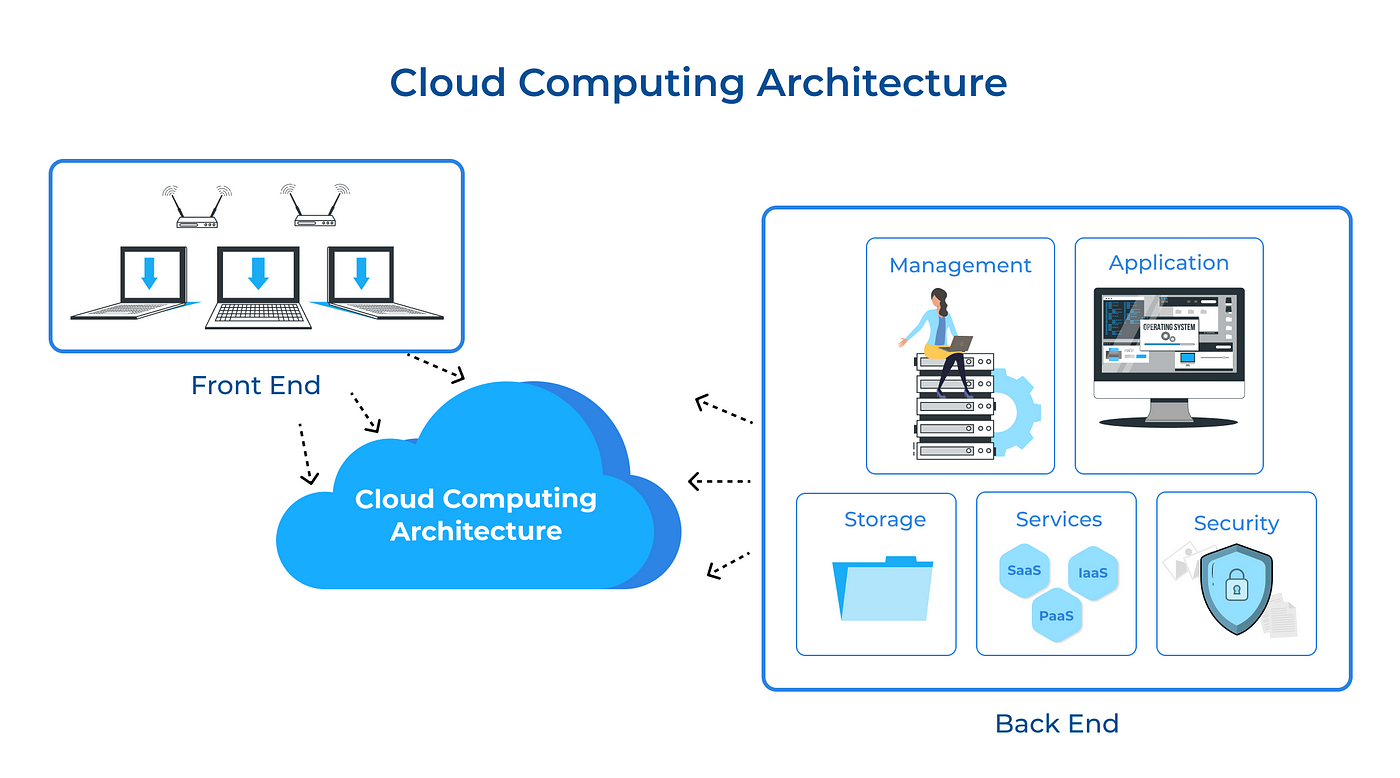
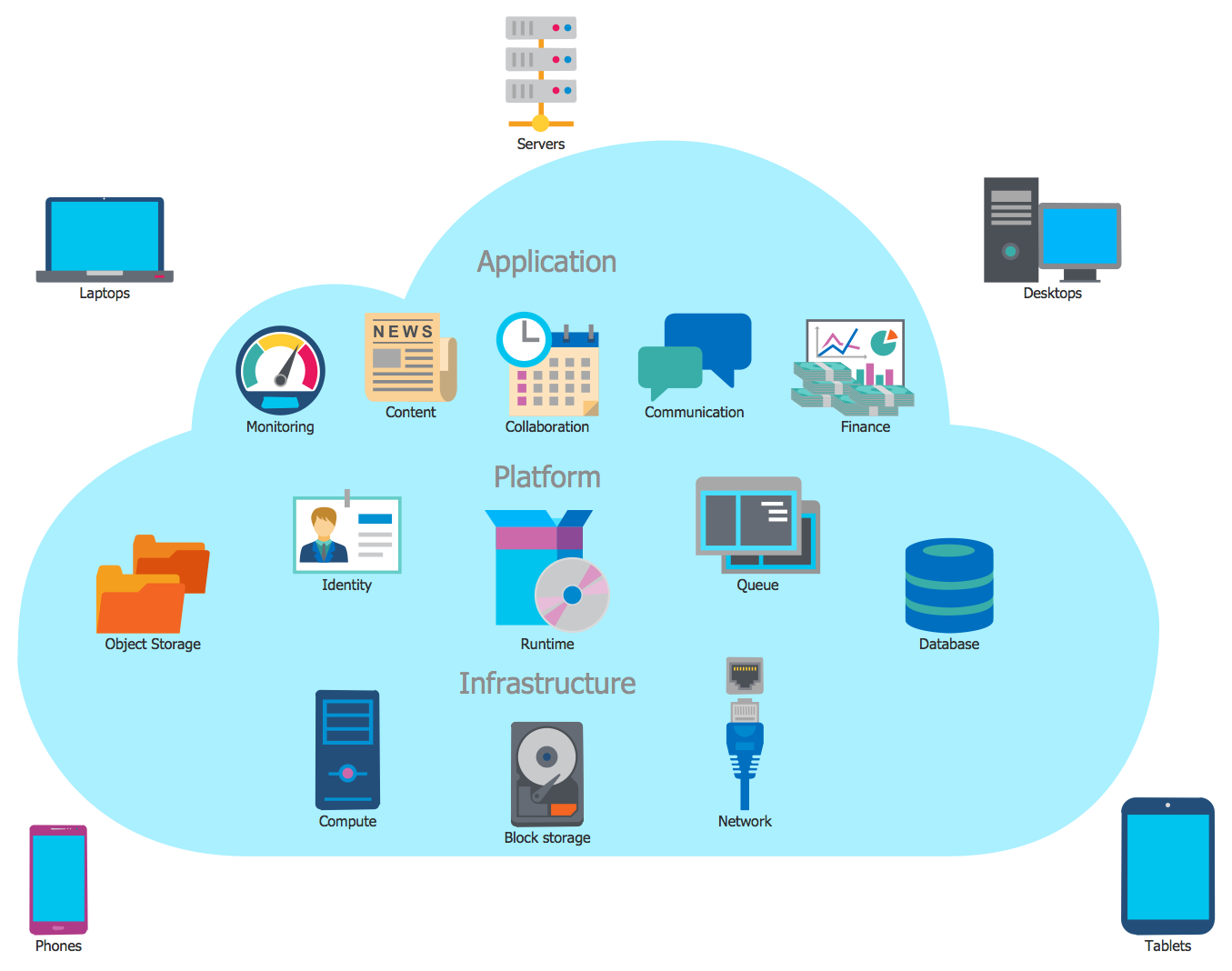
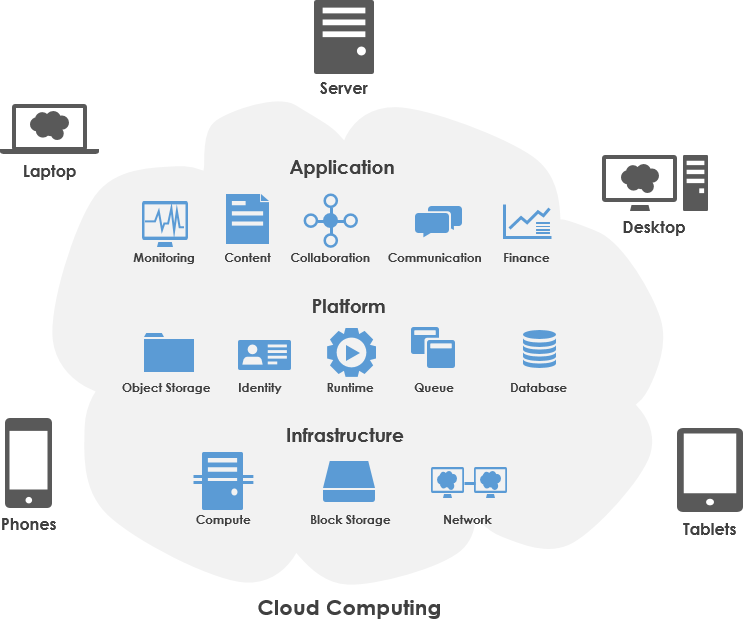
Cloud Infrastructure Overview
I decided to transition from a traditional Network Development approach to a more robust Cloud Infrastructure model for Industry Exams Plus. This shift provides better reliability, easier scalability, and improved security for our wide array of services, including web servers, mail servers, databases, proxies, and more.
By leveraging Amazon EC2, I’ve established a powerful virtual machine (VM) that runs multiple core functions, ensuring continuous uptime and rapid global accessibility.